Open Source
Is Source 2 FINALLY Coming to CSGO?
Despite moving Dota 2 over to the new engine in 2015, Valve have long been silent on whether CS would ever receive the same treatment. In early 2020, however, rumors began to circulate that the port was finally on its way. Now, further reports suggest a timeline for when fans might expect the arrival of Source 2.
Meanwhile, cryptic tweets from the developers suggest there’s something in the works more immediately – but exactly what it might be remains to be seen. Speculation abounds as to map updates, 128 servers, and more – catch up on the latest details in this video.
SUBSCRIBE TO OUR CHANNELS:
► Dexerto Esports – https://youtube.com/Dexerto
► Dexerto Call of Duty – https://www.youtube.com/DexertoCallofDuty
FOLLOW DEXERTO ON SOCIAL MEDIA:
► Twitter – https://twitter.com/Dexerto
► Instagram – https://instagram/Dexerto
► Facebook – https://facebook.com/Dexerto
► YouTube – https://youtube.com/Dexerto
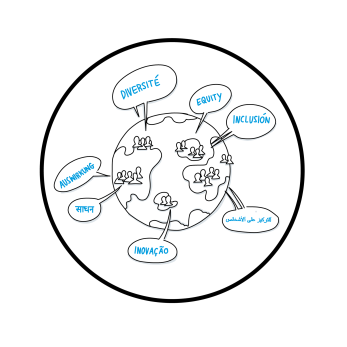
Our Evolution and Growth as a Movement- The ESEAP Story!
Drupal Core News: New provisional Drupal 7 maintainer: poker10
I am pleased to announce that Juraj Nemec (poker10) has accepted our invitation to become a provisional Drupal 7 core maintainer!
Juraj is based in Slovakia and has been working with Drupal for more than 12 years. He works at ActivIT as the Tech Lead and Senior Drupal developer. As a backend specialist, he most likes optimizing large-scale systems, performance tuning and digging into what can be improved to bring the best user experience.
He recently contributed to fixing Drupal 7’s PostgreSQL tests, helped to improve PostgreSQL performance with several important backports, and is actively working on improving Drupal 7’s compatibility with PHP 8.1 and 8.2. He is also helping to get the jQuery Update module ready for its first big update in several years.
Juraj is excited about the opportunity to contribute to the Drupal community. He will work with the Drupal 7 maintainer team (Fabianx and mcdruid).
Please join me in welcoming Juraj to the committer team!
Released command_kit 0.4.0
$EDITOR), also printing key/value fields, bulleted lists, and tables in a variety of formats (see examples/printing/tables.rb)!Ruby 3.2.0 Preview 3 Released
We are pleased to announce the release of Ruby 3.2.0-preview3. Ruby 3.2 adds many features and performance improvements.
WASI based WebAssembly support
This is an initial port of WASI based WebAssembly support. This enables a CRuby binary to be available on Web browser, Serverless Edge environment, and other WebAssembly/WASI embedders. Currently this port passes basic and bootstrap test suites not using Thread API.

Background
WebAssembly (Wasm) is originally introduced to run programs safely and fast in web browsers. But its objective – running programs efficinently with security on various environment – is long wanted not only by web but also by general applications.
WASI (The WebAssembly System Interface) is designed for such use cases. Though such applications need to communicate with operating systems, WebAssembly runs on a virtual machine which didn’t have a system interface. WASI standardizes it.
WebAssembly/WASI Support in Ruby intends to leverage those projects. It enables Ruby developers to write applications which runs on such promised platform.
Use case
This support encourages developers can utilize CRuby in WebAssembly environment. An example use case of it is TryRuby playground’s CRuby support. Now you can try original CRuby in your web browser.
Technical points
Today’s WASI and WebAssembly itself has some missing features to implement Fiber, exception, and GC because it’s still evolving and also for security reasons. So CRuby fills the gap by using Asyncify, which is a binary transformation technique to control execution in userland.
In addition, we built a VFS on top of WASI so that we can easily pack Ruby apps into a single .wasm file. This makes distribution of Ruby apps a bit easier.
Related links
Regexp improvements against ReDoS
It is known that Regexp matching may take unexpectedly long. If your code attempts to match an possibly inefficient Regexp against an untrusted input, an attacker may exploit it for efficient Denial of Service (so-called Regular expression DoS, or ReDoS).
We have introduced two improvements that significantly mitigate ReDoS.
Improved Regexp matching algorithm
Since Ruby 3.2, Regexp’s matching algorithm has been greatly improved by using memoization technique.
# This matching takes 10 sec. in Ruby 3.1, and does 0.003 sec. in Ruby 3.2
/^a*b?a*$/ =~ "a" * 50000 + "x"
The improved matching algorithm allows most of Regexp matching (about 90% in our experiments) to be completed in linear time.
(For preview users: this optimization may consume memory proportional to the input length for each matching. We expect no practical problems to arise because this memory allocation is usually delayed, and a normal Regexp matching should consume at most 10 times as much memory as the input length. If you run out of memory when matching Regexps in a real-world application, please report it.)
The original proposal is https://bugs.ruby-lang.org/issues/19104
Regexp timeout
The optimization above cannot be applied to some kind of regular expressions, such as including advanced features (e.g., back-references or look-around), or with huge fixed number of repetitions. As a fallback measure, a timeout feature for Regexp matching is also introduced.
Regexp.timeout = 1.0
/^a*b?a*()1$/ =~ "a" * 50000 + "x"
#=> Regexp::TimeoutError is raised in one second
Note that Regexp.timeout is a global configuration. If you want to use different timeout settings for some special Regexps, you may want to use timeout keyword for Regexp.new.
Regexp.timeout = 1.0
# This regexp has no timeout
long_time_re = Regexp.new("^a*b?a*()1$", timeout: Float::INFINITY)
long_time_re =~ "a" * 50000 + "x" # never interrupted
The original proposal is https://bugs.ruby-lang.org/issues/17837
Other Notable New Features
No longer bundle 3rd party sources
-
We no longer bundle 3rd party sources like
libyaml,libffi.-
libyaml source has been removed from psych. You may need to install
libyaml-devwith Ubuntu/Debian platfrom. The package name is different each platforms. -
bundled libffi source is also removed from
fiddle
-
Language
-
Anonymous rest and keyword rest arguments can now be passed as
arguments, instead of just used in method parameters.
[Feature #18351]def foo(*) bar(*) end def baz(**) quux(**) end -
A proc that accepts a single positional argument and keywords will
no longer autosplat. [Bug #18633]proc{|a, **k| a}.call([1, 2]) # Ruby 3.1 and before # => 1 # Ruby 3.2 and after # => [1, 2] -
Constant assignment evaluation order for constants set on explicit
objects has been made consistent with single attribute assignment
evaluation order. With this code:foo::BAR = bazfoois now called beforebaz. Similarly, for multiple assignments
to constants, left-to-right evaluation order is used. With this
code:foo1::BAR1, foo2::BAR2 = baz1, baz2The following evaluation order is now used:
foo1foo2baz1baz2
-
Find pattern is no longer experimental.
[Feature #18585] -
Methods taking a rest parameter (like
*args) and wishing to delegate keyword
arguments throughfoo(*args)must now be marked withruby2_keywords
(if not already the case). In other words, all methods wishing to delegate
keyword arguments through*argsmust now be marked withruby2_keywords,
with no exception. This will make it easier to transition to other ways of
delegation once a library can require Ruby 3+. Previously, theruby2_keywords
flag was kept if the receiving method took*args, but this was a bug and an
inconsistency. A good technique to find the potentially-missingruby2_keywords
is to run the test suite, for where it fails find the last method which must
receive keyword arguments, useputs nil, caller, nilthere, and check each
method/block on the call chain which must delegate keywords is correctly marked
asruby2_keywords. [Bug #18625] [Bug #16466]def target(**kw) end # Accidentally worked without ruby2_keywords in Ruby 2.7-3.1, ruby2_keywords # needed in 3.2+. Just like (*args, **kwargs) or (...) would be needed on # both #foo and #bar when migrating away from ruby2_keywords. ruby2_keywords def bar(*args) target(*args) end ruby2_keywords def foo(*args) bar(*args) end foo(k: 1)
Performance improvements
YJIT
- Support arm64 / aarch64 on UNIX platforms.
- Building YJIT requires Rust 1.58.1+. [Feature #18481]
Other notable changes since 3.1
- Hash
- Hash#shift now always returns nil if the hash is
empty, instead of returning the default value or
calling the default proc. [Bug #16908]
- Hash#shift now always returns nil if the hash is
- MatchData
- MatchData#byteoffset has been added. [Feature #13110]
- Module
- Module.used_refinements has been added. [Feature #14332]
- Module#refinements has been added. [Feature #12737]
- Module#const_added has been added. [Feature #17881]
- Proc
- Proc#dup returns an instance of subclass. [Bug #17545]
- Proc#parameters now accepts lambda keyword. [Feature #15357]
- Refinement
- Refinement#refined_class has been added. [Feature #12737]
- RubyVM::AbstractSyntaxTree
- Add
error_tolerantoption forparse,parse_fileandof. [[Feature #19013]]
- Add
- Set
- Set is now available as a builtin class without the need for
require "set". [Feature #16989]
It is currently autoloaded via theSetconstant or a call toEnumerable#to_set.
- Set is now available as a builtin class without the need for
- String
- String#byteindex and String#byterindex have been added. [Feature #13110]
- Update Unicode to Version 14.0.0 and Emoji Version 14.0. [Feature #18037]
(also applies to Regexp) - String#bytesplice has been added. [Feature #18598]
- Struct
- A Struct class can also be initialized with keyword arguments
withoutkeyword_init: trueonStruct.new[Feature #16806]
- A Struct class can also be initialized with keyword arguments
Compatibility issues
Note: Excluding feature bug fixes.
Removed constants
The following deprecated constants are removed.
FixnumandBignum[Feature #12005]Random::DEFAULT[Feature #17351]Struct::GroupStruct::Passwd
Removed methods
The following deprecated methods are removed.
Dir.exists?[Feature #17391]File.exists?[Feature #17391]Kernel#=~[Feature #15231]Kernel#taint,Kernel#untaint,Kernel#tainted?
[Feature #16131]Kernel#trust,Kernel#untrust,Kernel#untrusted?
[Feature #16131]
Stdlib compatibility issues
Psychno longer bundles libyaml sources.
Users need to install the libyaml library themselves via the package
system. [Feature #18571]
C API updates
Updated C APIs
The following APIs are updated.
- PRNG update
rb_random_interface_tupdated and versioned.
Extension libraries which use this interface and built for older versions.
Alsoinit_int32function needs to be defined.
Removed C APIs
The following deprecated APIs are removed.
rb_cDatavariable.- “taintedness” and “trustedness” functions. [Feature #16131]
Standard libraries updates
-
SyntaxSuggest
- The feature of
syntax_suggestformerlydead_endis integrated in Ruby.
[Feature #18159]
- The feature of
-
ErrorHighlight
- Now it points an argument(s) of TypeError and ArgumentError
test.rb:2:in `+': nil can't be coerced into Integer (TypeError)
sum = ary[0] + ary[1]
^^^^^^
- The following default gems are updated.
- RubyGems 3.4.0.dev
- bigdecimal 3.1.2
- bundler 2.4.0.dev
- cgi 0.3.2
- date 3.2.3
- error_highlight 0.4.0
- etc 1.4.0
- io-console 0.5.11
- io-nonblock 0.1.1
- io-wait 0.3.0.pre
- ipaddr 1.2.4
- json 2.6.2
- logger 1.5.1
- net-http 0.2.2
- net-protocol 0.1.3
- ostruct 0.5.5
- psych 5.0.0.dev
- reline 0.3.1
- securerandom 0.2.0
- set 1.0.3
- stringio 3.0.3
- syntax_suggest 0.0.1
- timeout 0.3.0
- The following bundled gems are updated.
- minitest 5.16.3
- net-imap 0.2.3
- rbs 2.6.0
- typeprof 0.21.3
- debug 1.6.2
- The following default gems are now bundled gems.
See NEWS
or commit logs
for more details.
With those changes, 2719 files changed, 191269 insertions(+), 120315 deletions(-)
since Ruby 3.1.0!
Download
-
https://cache.ruby-lang.org/pub/ruby/3.2/ruby-3.2.0-preview3.tar.gz
SIZE: 20086542 SHA1: dafca8116d36ceaa32482ab38359768de8c3ae5e SHA256: c041d1488e62730d3a10dbe7cf7a3b3e4268dc867ec20ec991e7d16146640487 SHA512: 860634d95e4b9c48f18d38146dfbdc3c389666d45454248a4ccdfc3a5d3cd0c71c73533aabf359558117de9add1472af228d8eaec989c9336b1a3a6f03f1ae88 -
https://cache.ruby-lang.org/pub/ruby/3.2/ruby-3.2.0-preview3.tar.xz
SIZE: 14799804 SHA1: c94e2add05502cb5c39afffc995b7c8f000f7df0 SHA256: d3f5619de544240d92a5d03aa289e71bd1103379622c523a0e80ed029a74b3bb SHA512: c1864e2e07c3711eaa17d0f85dfbcc6e0682b077782bb1c155315af45139ae66dc4567c73682d326975b0f472111eb0a70f949811cb54bed0b3a816ed6ac34df -
https://cache.ruby-lang.org/pub/ruby/3.2/ruby-3.2.0-preview3.zip
SIZE: 24426893 SHA1: 346c051c4be7ab8d0b551fd2ff8169785697db62 SHA256: cf49aa70e7ebd8abebffd5e49cd3bd92e5b9f3782d587cc7ed88c98dd5f17069 SHA512: 4f22b5ea91be17ef5f68cf0acb1e3a226dcc549ad71cc9b40e623220087c4065ca9bea942710f668e5c94ca0323da8d2ccd565f95a9085c1a0e38e9c0543b22f
What is Ruby
Ruby was first developed by Matz (Yukihiro Matsumoto) in 1993,
and is now developed as Open Source. It runs on multiple platforms
and is used all over the world especially for web development.
Posted by naruse on 11 Nov 2022
FreeBSD 12.4-RC2 Available
OpenPOWER Foundation and Community Members to showcase at SC22 Conference in Dallas, TX!
Published on Thursday 10 November 2022 Next week, OPF will be exhibiting at the SC22 conference in Dallas, TX. OPF will be showcasing our LibreBMC project and talking about all things open hardware and software. The best part is that we won’t be alone, as we have a number of OPF community members and partners showcasing at […]
The post OpenPOWER Foundation and Community Members to showcase at SC22 Conference in Dallas, TX! appeared first on Linux.com.